
Docker has announced that it is open sourcing its catalog of over 1,000 Docker Hardened Images (DHI), which are production-ready images maintained by Docker to reduce vulnerabilities in container images.
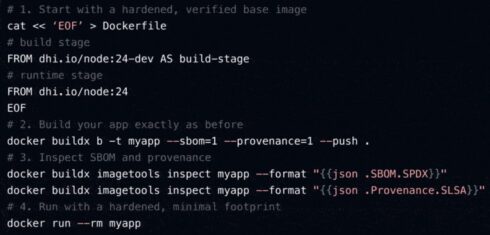
Each image includes a complete software bill of materials (SBOM), transparent public CVE data, SLSA Build Level 3 provenance, and cryptographic proof of authenticity.
Available under the Apache 2.0 license, DHI is built on Debian and Alpine, allowing anyone to adopt the images without lock-in and with minimal changes to their existing workflows, Docker explained.
According to the company, the main impetus behind deciding to open source the DHI catalog was to enable everyone from maintainers to hobbyists to governments to gain access to these secure images without restrictions.
“Today’s announcement marks a watershed moment for our industry. Docker is fundamentally changing how applications are built-secure by default for every developer, every organization, and every open-source project,” Christian Dupuis, senior principal software engineer at Docker, wrote in a blog post.
Docker says that its AI assistant will be able to scan a customer’s existing containers and recommend the equivalent hardened images to replace what they currently have.
Organizations that need additional support or services will be able to purchase DHI Enterprise or Extended Lifecycle Support. DHI Enterprise promises remediation of critical vulnerabilities in under seven days, FIPS-enabled and STIG-ready images, and full customization. Extended Lifecycle Support is an add-on to DHI Enterprise that comes with five years of support after the upstream support ends, ongoing signing and auditability, and continued CVE patches, SBOM updates, and provenance attestations.
Additionally, Docker has built Hardened Helm Charts that make use of DHIs in Kubernetes environments, as well as Hardened MCP Servers, including MongoDB, Grafana, and GitHub. It also plans to continue this work in the coming months, with hardened libraries, hardened system packages, and other secure components. “The goal is simple: be able to secure your application from main() down,” Docker wrote.




